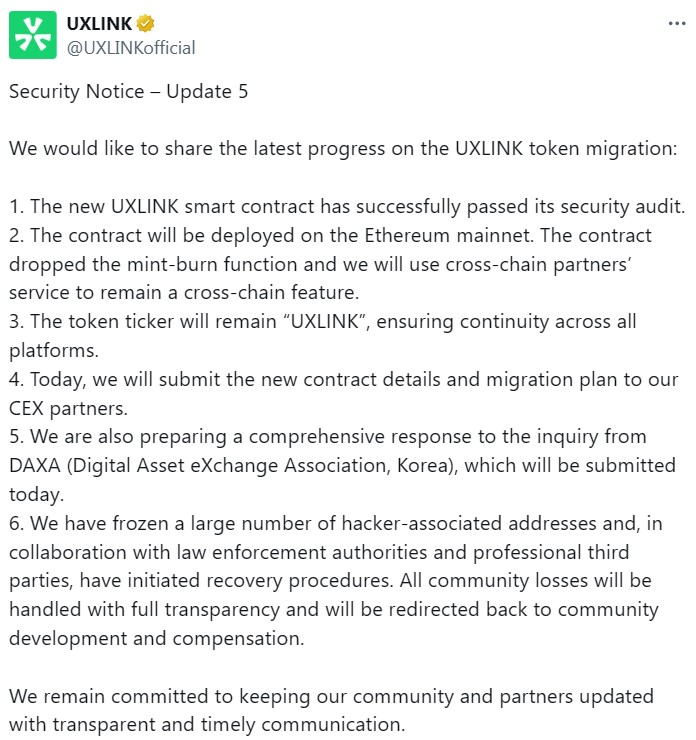
Decentralized social platform Uxlink said Wednesday it is rolling out new Ethereum contracts through a multi-signature wallet exploit after attackers mint billions of unauthorized tokens and crash the value of their native assets.
Uxlink said the new smart contract will pass a security audit and will be deployed to Ethereum Mainnet. The project said the new contract reduced the function of mintburn to prevent similar incidents in the future.
The project confirmed the violations on Tuesday, saying a significant amount of code had been transferred to the exchange. Estimates of losses from hacks vary, with Cyvers alerts stolen at least $11 million, and Hacken placed figures above $30 million.
What’s clear is that the incident highlighted the flaws in smart contract security that the project should deal with. Marwan Hachem, co-founder and CEO of Web3 security company Fearsoff, told Cointelegraph that the incident underscored the risk of rushing forward without the necessary security layer.
Uxlink Exploit highlights “centralized control” risk
The attacker controlled Uxlink’s smart contracts through multi-signature wallet violations, initially minted 2 billion Uxlink tokens. The price of the token fell 90% from $0.33 to $0.033 as the attackers continued to build it.
Hachem told Cointelegraph that the Uxlink violation came from a vulnerability in a multi-signature wallet. This allowed hackers to execute arbitrary code and take over the management of contracts. He added that this will lead to fraudulent token mints.
“This highlights some design flaws in the Uxlink setup,” Hachem told Cointelegraph. “The multi-signature wallet, LAX, which was not properly protected from delegate call exploits, controls who can combine built-in code to implement the supply cap.”
Hachem said this “showns a dangerous point to maintaining too much centralized control in projects that claim to be decentralized.
Related: Private user data reports are “unfounded” according to crypto.com
Time lock, hardcoded cap, the need for better audits
From a technical standpoint, Hachem said the Uxlink hack could have been avoided by several standard safeguards.
This includes creating new tokens and adding time locks to sensitive actions such as changing contract ownership. “The 24-48 hour delay gives the community the opportunity to find something unusual before it passes,” Hachem said.
The second solution involved waiving mint privileges after the token was launched, so even the insider couldn’t make more. Hachem said that the hard coding supply cap for smart contracts prevents them from blocking the risk of new tokens.
Operationally, Hachem emphasized the importance of independent reviews and continuous transparency.
“You can’t audit token contracts. Multisig setups also require scrutiny,” he said.
According to Hachem, the wider lesson was that even commonly used tools such as Multisig wallets should not be treated as bulletproof. He said emergency stops for critical functions are also of the utmost importance in pursuit of more decentralized governance.
“The Uxlink incident highlights that moving forward without solid and continuous security can shatter the confidence of the community. It’s better to have multiple defenses from the start,” Hachem told Cointelegraph.
magazine: XRP is Thailand’s top performance asset. Shanghai Dumpfil: Asia Express