Crypto security experts have identified a recent sophisticated phishing campaign targeting prominent figures on X (formerly Twitter). Unlike traditional scams, this campaign employs advanced tactics that bypass two-factor authentication, making it particularly dangerous. The attack leverages X’s unique infrastructure to gain unauthorized access to well-known accounts and raises concerns about new vulnerabilities within social media platforms that are valued by the crypto community.
- The new phishing campaign targets X accounts of cryptographic personalities by leveraging X infrastructure to bypass two-factor authentication.
- The attack uses compelling messaging and metadata tricks to create highly reliable phishing links that mimic Google Calendar.
- Experts warn that the campaign could be part of a broader effort to compromise social media accounts in the crypto sector.
- The scam includes fake approval requests that require extensive account permissions, raising doubt among vigilant users.
- Recommendations include carefully examining suspicious connected app revocations and unusual permission requests to prevent account compromise.
A new wave of phishing campaigns targets industry-image social media accounts within the cryptocurrency community, and threats in the digital assets ecosystem are rising. These scams demonstrate the ability to use X’s proprietary infrastructure to exploit account takeovers to avoid two-factor authentication. This method highlights the evolving refinement of attack vectors targeted at crypto influencers and traders.
As reported by Crypto developer Zak Cole, the attack does not rely on traditional means such as fake login pages or password theft. Instead, it utilizes support features within the X app itself to steal account control without the need for victim passwords or 2FA. This prompted warnings from security researchers and called for increased vigilance. Oham Shah of Metamask Security Researcher confirmed that he saw the attack being “wild” active.
Create a compelling phishing message
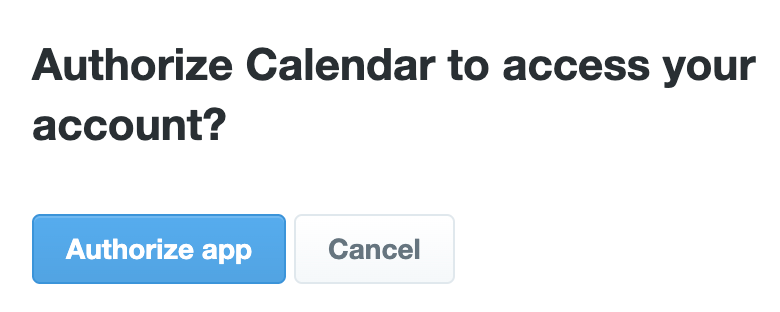
The standout feature of the campaign is its ability to look authentic. The attacker begins contacting you via a direct message that contains a link that appears to direct the user to a legitimate service. The link appears to lead to the Google Calendar domain thanks to the way X uses metadata to generate post previews. In reality, the link is directed to a domain registered as “x(.)ca-lendar(.)com” but was registered a few days ago, but the preview shows the familiar Google Calendar URL, ensuring that users trust the link.
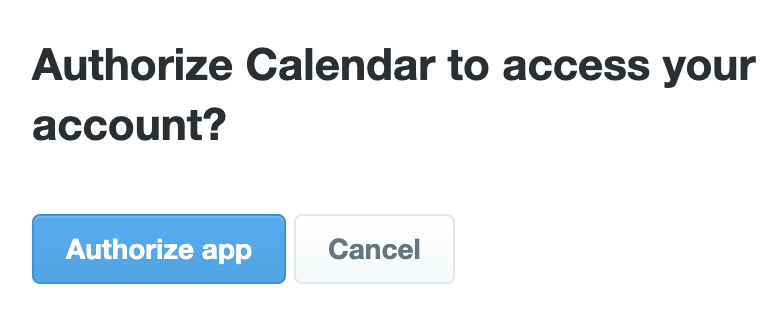
When clicked, the link will redirect you to the X approval page and request permission from the app called “Calendar” to access your account. In a thorough inspection, the app’s name contains two Cyrillic letters, similar to the Latin “A” and “E,” a subtle trick designed to avoid detection. An approval request prompts users to grant extensive permissions, including editing the following accounts, posts, profile information, and more: All of these are questionable for the calendar app.

Detects signs of phishing attacks
One of the most subtle signs of fraud is the fleeting appearance of the URL, and it is easy to overlook that it appears to be visible only before a redirect. However, the key metric is the scope of the requested authority. This app is very rare in the calendar app.
In addition to doubt, users are redirected to Calendly.com after granting permission, revealing inconsistencies that encourage skepticism. “They infuse Google Calendar, but were they redirected to Calendly? Operational security failures,” Cole pointed out. To prevent a compromise on your account, he recommends reviewing connected apps on the X settings page and canceling what is called a “calendar,” especially what you think is suspicious.
The complexity of this attack shows the importance of maintaining a cautious attitude towards social media permission, especially within the cryptocurrency realm where influential accounts can significantly sway market sentiment. As the crypto market remains unstable, it is more important than ever to protect these digital assets from social engineering tactics.