According to a new on-chain analysis, the attackers’ on-chain transactions behind the $116 million Balancer hack demonstrate sophisticated attackers and extensive preparation that may have taken months to orchestrate without leaving a trace.
The decentralized exchange (DEX) and automated market maker (AMM) balancer was exploited with approximately $116 million worth of digital assets on Monday.
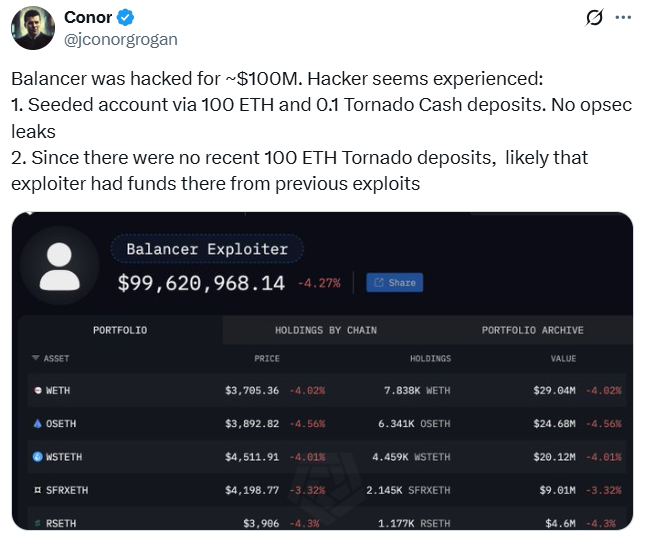
Blockchain data shows that the attacker discreetly funded the account using a small 0.1 Ether (ETH) deposit from cryptocurrency mixer Tornado Cash to avoid detection. Conor Grogan, a director at Coinbase, said the abuser had at least 100 ETH stored in the Tornado Cash smart contract, suggesting a possible link to previous hacks.
“The hacker appears to be experienced. 1. Seed account with 100 ETH and 0.1 Tornado Cash. No opsec leaks,” Grogan said in a Monday X post. “There were no recent 100 ETH Tornado deposits, so the exploiters may have had funds there from previous exploits.”
Grogan points out that users rarely store such large sums of money in privacy mixers, further hinting at the professionalism of the attackers.
Balancer offered the abusers a 20% white hat reward if the stolen funds were returned in full, less compensation, by Wednesday.
Related: Balancer Audit comes under scrutiny after more than $100 million in abuse
“Our team is working with leading security researchers to understand this issue and will share additional findings and a full post-mortem as soon as possible,” Balancer said in its latest X update on Monday.
Balancer exploits were the most sophisticated attacks of 2025: Cyvers
According to Deddy Lavid, co-founder and CEO of blockchain security company Cyvers, the Balancer exploit is one of the “most sophisticated attacks we’ve seen this year.”
“The attackers bypassed the access control layer and directly manipulated asset balances. This was a critical failure in operational governance, not core protocol logic.”
Ravid said the attack shows that static code auditing is no longer sufficient. Instead, it called for continuous real-time monitoring to alert people to suspicious financial flows before they leave.
Related: “SEAL” team intercepts 60 fake IT employees with ties to North Korea, CZ sounds alarm
Lazarus Group suspends illegal activities for months ahead of $1.4 billion Bybit hack
North Korea’s notorious Lazarus Group is also known for its extensive preparations before major hacks.
According to blockchain analysis firm Chainalysis, illegal activities related to North Korean cyber attackers have sharply declined since July 1, 2024, despite a spike in attacks earlier that year.
Eric Jardine, head of cybercrime research at Chainalysis, said the significant slowdown before the Bybit hack shows that state-sponsored hacking groups are “regrouping to select new targets.”
“The slowdown we observed could have been a reorganization to select new targets or investigate infrastructure, or it could have been related to those geopolitical events,” he told Cointelegraph.
Cointelegraph reported on March 4 that it took Lazarus Group 10 days to launder 100% of Bybit funds stolen through decentralized cross-chain protocol THORChain.
magazine: Coinbase hack shows the law probably won’t protect you — here’s why