Batch Threshold Encryption (BTE) builds on fundamental concepts such as threshold encryption to enable secure collaboration between multiple parties without exposing sensitive data to a single participant. BTE is an evolution of earlier TE encrypted memory schemes, such as Shutter, which was previously discussed. For now, all existing research on BTE remains at the prototype or research stage, but if successful, it could shape the future of distributed ledgers. This creates clear opportunities for further research and potential adoption. We will discuss this in detail in this article.
In modern blockchains, transaction data is published in a mempool before being ordered, executed, and confirmed within blocks. This transparency creates an avenue for sophisticated actors to engage in extractive practices known as Maximum Extractable Value (MEV). MEV leverages the ability of block proponents to reorder, include, or omit transactions for financial gain.
Typical MEV exploits such as front-running and sandwich attacks remain prevalent, especially on Ethereum, where an estimated $2.9 million was extracted during the October 10 flash crash. Approximately 32% of these attacks were privately relayed to miners, and some involved more than 200 chained subtransactions in a single exploit, so it remains difficult to accurately measure the total MEV extracted.
Some researchers are trying to thwart MEV with memory pool designs where pending transactions are kept encrypted until block finalization. This prevents other blockchain participants from seeing what transactions or actions a trading user is attempting to perform. Many encrypted memory pool proposals use some form of threshold encryption (TE) for this purpose. TE splits the private key, which can expose transaction data, across multiple servers. Similar to multisig, a minimum number of signers must work together to combine the key agreement and unlock the data.
Why BTE is important
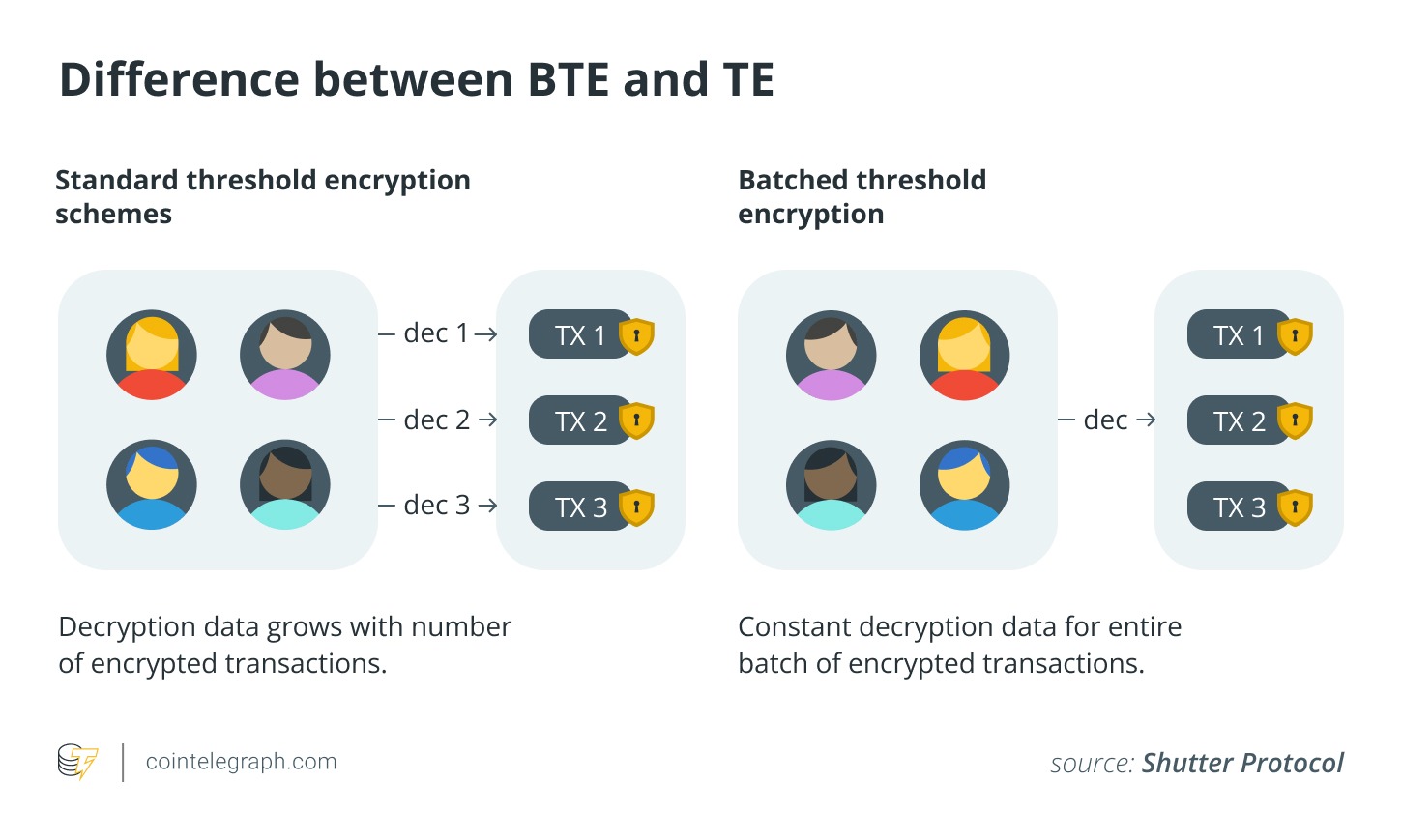
Standard TE is difficult to scale efficiently because it requires every server to decrypt each transaction individually and broadcast a partial decryption share. These individual shares are recorded on-chain for aggregation and verification. This creates server communication load, slows down the network, and increases chain congestion. BTE solves this limitation by allowing each server to release a single, fixed-sized decryption share that unlocks the entire batch, regardless of size.
The first functional version of BTE (2024), developed by Arka Rai Choudhuri, Sanjam Garg, Julien Piet, and Guru-Vamsi Policharla, used the so-called KZG commitment scheme. This allows the server committee to lock a polynomial function to its public key, keeping the function initially hidden from both users and committee members.
To decrypt a transaction encrypted with a public key, you need to prove that the transaction fits a polynomial. Since a polynomial of fixed degree can be fully determined from a set number of points, the server only needs to collectively exchange small amounts of data to provide this proof. Once a sharing curve is established, a single compact piece of information derived from it can be sent to unlock all transactions in the batch at once.
Importantly, transactions that do not fall within the polynomial remain locked, allowing the commission to selectively expose a subset of encrypted transactions while hiding others. This ensures that all encrypted transactions other than the batch you select for execution remain encrypted.
Therefore, current TE implementations such as Ferveo and MEVade can integrate BTE to protect the privacy of non-batch transactions. BTE is also a natural fit for layer 2 rollups such as Metis, Espresso, and Radius. These rollups already strive for fairness and privacy through time-delayed encryption and trusted sequencers. Using BTE, these rollups enable a trustless ordering process and prevent the abuse of transaction visibility for arbitrage or liquidation profits.
However, this first version of BTE had two major drawbacks. Each time a new batch of transactions was encrypted, a complete reinitialization of the system was required, including a new round of key generation and parameter settings. Decryption consumed a large amount of memory and processing power as nodes worked to combine all partial shares.
Both of these factors limited the practicality of BTE. For example, committee updates and block operations require frequent execution of the DKG, making this scheme effectively prohibitive for moderately sized permissioned committees, much less attempting to scale it to unpermitted networks.
In the case of selective decryption, where validators only decrypt profitable transactions, BTE makes all decryption shares publicly verifiable. This allows anyone to detect cheating and punish criminals with slashes. As long as the honest server threshold is active, the process remains reliable.
Upgrade to BTE
Choudhuri, Garg, Policcharla, and Wang (2025) made the first upgrade to BTE to improve server communication through a scheme called one-time setup BTE. This scheme required only an initial distributed key generation (DKG) ceremony performed once between all decryption servers. However, a multiparty computation protocol was still required to set the commitment for each batch.
The first truly breakthrough BTE scheme arrived in August 2025, when Bormet, Faust, Othman, and Qu introduced BEAT-MEV as a single, one-time initialization that could support all future batches. This is achieved using two advanced tools: punctureable pseudo-random number functions and threshold homomorphic encryption, which allow servers to reuse the same setup parameters indefinitely. Each server only needs to send a small amount of data when decrypting, keeping server communication costs low.
Summary of expected performance
Later, another paper called BEAST-MEV introduced the concept of Silent Batched Threshold Encryption (SBTE), which eliminated the need for interactive setup between servers. This replaces iterative tuning with a non-interactive, universal, one-time setup that allows nodes to work independently.
However, combining all partial decodings later still requires a large amount of interactive computation. To fix this, BEAST-MEV borrowed BEAT-MEV’s sub-batch technique and used parallel processing to allow the system to decode large batches (up to 512 transactions) in less than a second. The following table summarizes how each subsequent BTE design improves on the original BTE design.
The potential for BTE also applies to protocols such as CoW Swap, which already mitigates MEV through batch auctions and intent-based matching, but exposes a portion of the order flow to a public memory pool. Integrating BTE before solver submission bridges that gap and provides end-to-end transaction privacy. For now, Shutter Network is the most likely candidate for early adoption, with other protocols likely to follow as implementation frameworks become more mature.
This article does not contain investment advice or recommendations. All investment and trading moves involve risk and readers should conduct their own research when making decisions.
This article is for general informational purposes only and is not intended to be, and should not be taken as, legal or investment advice. The views, ideas, and opinions expressed herein are those of the author alone and do not necessarily reflect or represent the views and opinions of Cointelegraph.
Cointelegraph does not endorse the content of this article or the products mentioned here. Readers should do their own research before taking any action related to the products or companies mentioned and are solely responsible for their decisions.