A guide to 51% attacks on blockchain networks.
In the world of cryptocurrencies, where hacking, social engineering, malicious software, and even fraudulent on-chain transfer requests abound, there is one threat that stands out in terms of its scale and its targeting of the entire blockchain ecosystem. That’s a 51% attack.
A 51% attack on a blockchain network refers to a type of exploit where an individual or group controls more than half (at least 51%) of the network consensus. This type of attack typically refers to blockchains that use proof-of-work (PoW) consensus, where miners verify transactions, such as Bitcoin (BTC) and Ethereum Classic (ETC). For PoW chains, a 51% attack involves taking control of a large portion of the mining power, forcing the attacker to manipulate the chain.
The potential for such attacks is related to the very nature of cryptocurrencies: decentralization. Unlike traditional financial systems such as banks, where a central authority controls and verifies all transactions, blockchain relies on a decentralized network of miners, or validators, to maintain consensus, a system in which a majority agrees on which transactions are valid.
Decentralization makes cryptocurrencies innovative, but it also opens the door to the risks of centralized control if one group gains more control than necessary.
Can a 51% attack occur on a PoS network?
Theoretically, a 51% attack could occur in a proof-of-stake (PoS) network. For networks like Ethereum, which has moved from proof-of-work to proof-of-stake consensus, a 51% attack would require a malicious attacker to control more than half of the network’s staked tokens, rather than the mining power.
However, while technically possible, such an attack would be much more difficult and risky to carry out, given that a malicious validator could reduce staked tokens, making it an economically self-destructive attack.
51% What happens during an attack?
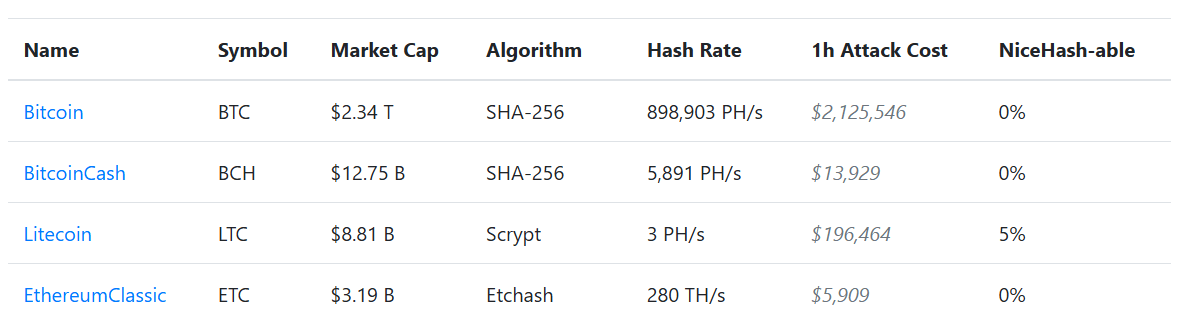
Once in control of a majority of the network, an attacker could prevent new transactions from being confirmed, stop payments, or reverse transactions. Large networks like Bitcoin are more secure because no single group can easily control most of the computing power, given the prohibitive costs and difficulty of mining.

However, smaller chains are much more vulnerable as mining power can be rented relatively cheaply for short periods of time through services like NiceHash, significantly reducing the cost of carrying out such attacks.
Data from Crypto51, which tracks the current cost of 51% attacks across various networks, shows that as of October 2025, a 24-hour attack against Ethereum Classic would cost more than $144,000, while a similar attack against Bitcoin would cost around $53 million.
Privacy chain Monero fell victim to multiple network “reorganization” attacks (also known as reorgs) in August and September 2025, leading to speculation that the network may have been hit by 51%. In this incident, the mining pool associated with Qubic, a layer 1 chain, captured more than half of the hashing power and passed through the longer chain, undoing approximately 18 blocks and sending approximately 117-118 transactions back to the memory pool, resulting in delayed payments.
And such attacks are not uncommon. A report from MIT’s Digital Currents Initiative points out that between 2019 and 2020, there were more than 40 network reorganizations six or more blocks deep in coins such as BTG, HANA, VTC, XVG, EXP, and LCC.
What is a double-spend attack?
During a 51% attack, cryptocurrency exchanges are often the first to receive a signal, as the attacker may attempt to double-spend tokens, i.e. spend what appears to be the same asset multiple times. In this process, an attacker sends tokens from a chain they control to an exchange and clones them while manipulating the chain and erasing the initial payment.
Ethereum Classic, a hard fork of Ethereum that remained PoW, suffered multiple 51% attacks in 2019 and 2020, with some exchanges losing funds in double-spending incidents.
Here’s how it works: The hacker can send the coins to an outside party, such as an exchange, where they can be exchanged for another asset and turned into cash, but they can also secretly build another version of the exploited blockchain, and that particular transaction will be skipped. If the attacker’s new chain becomes longer, the network switches to it, effectively canceling the initial payment and allowing the hacker to use the same coins again.
As the team behind Ethereum Classic explained in a blog post, if a new alternate blockchain created by an attacker “has accumulated more work than the main chain” or has more activity, “all nodes in the ETC network will abandon the main chain they were working on and immediately adopt the new alternate chain built by the attacker.”
Effectively, an attacker participating in a 51% attack could walk away with both new on-chain assets under their control and the value gained by exchanging the dually spent assets on an exchange. As The Defiant previously reported, the attack on Ethereum Classic caused some exchanges such as Coinbase to delay confirmations to prevent attackers from cashing out, leaving users to wait more than 10 hours for ETC deposits.
Cybersecurity firm Hacken reminded in a statement that the infamous Bitcoin Gold attack in May 2018 allowed attackers to double-spend around $18 million.
Not necessarily 51%
The history of 51% attacks goes back even further. Early digital cash systems such as DigiCash and E-gold were designed to enable secure online payments without relying on traditional banks, but were still vulnerable to attack even if only about 33% of the nodes became malicious, a vulnerability now known as the Byzantine Generals Problem.
The introduction of the Nakamoto consensus mechanism using proof of work with Bitcoin raised the threshold for such attacks to 51%, tying security directly to computational strength rather than the number of nodes.
Ethereum Classic has also grown stronger over time. After Ethereum switched to proof-of-stake in 2022, some of its old mining power moved to ETC, increasing its hashrate from 24 TH/s to over 150 TH/s, making it the largest proof-of-work chain supporting smart contracts.
Stronger hashing power, better verification, and additional protections have made attacks such as double-spending much harder to perform on the network.
In reality, blockchain networks remain 51% risky, especially those with low total hash rates or networks with concentrated mining power, but their success depends on multiple factors, and large networks are becoming increasingly resilient. As the broader cryptocurrency ecosystem matures and grows, detection and response to these types of attacks are also improving.