Updated September 1st 11:30pm UTC: This article has been updated to include information from Halborn’s Chief Information Security Officer.
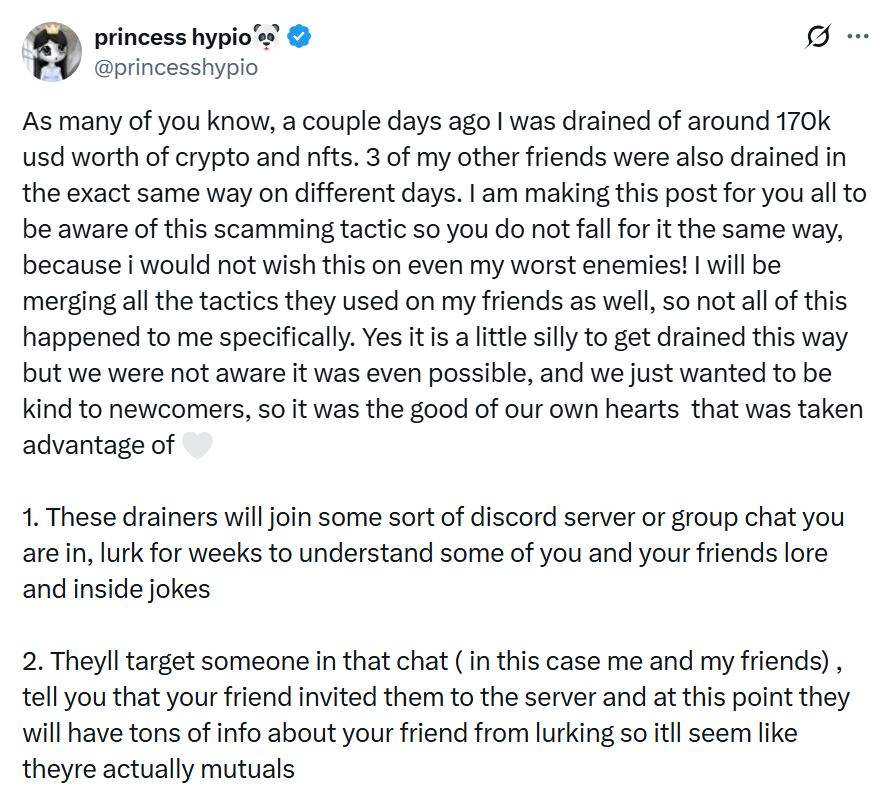
Last month, Crypto user and NFT artist Princess Hypio told followers he lost $170,000 on Crypto and fungible Token after convincing the scammer to play the game on Steam.
She was playing “unconsciously” with the con artist, but they secretly steal her funds and hacked her inconsistencies. She used the same tactics on three other friends, she wrote in an August 21 post on X.
After all, tactics have been around for a while, and some tactics are known as “Try My Game” scams.
Speaking to Nick Percoco’s Cointelegraph, Chief Security Officer at Kraken, he said these methods have become increasingly popular methods of attack.
“Try my game” hack: How it works
The encrypted version of a scam involves hackers joining a Discord server or group, lying in wait, learning how users interact and use that information to gain trust.
Hackers then ask users if they own crypto or NFTs, and often ask questions under the guise of interest and evaluate the digital assets they own. In Princess Hio’s case, they had Mirady NFTs, which resulted in her being targeted.
After identifying the target in Crypto, the hacker invites the victim to play the game and sends the link to the server using Trojan malware that provides access to the user device. This allows you to steal your personal information and drain connected wallets.
In the case of Princess Hypio, this trick involved offering to buy for her and convince her to download the Steam game. The game itself was safe, but the server on which the game was hosted was malicious.
She lost $170,000 in code and NFT in the attack, she said.
It was days after Discord released a policy explanator for deceptive practices, warning that promoting or enforcing financial fraud on social platforms would violate the terms of use.
“These scams don’t use code. They exploit trust. Attackers impersonate friends and pressure people to take actions that they don’t normally take,” says Percoco.
“The biggest vulnerability in cryptography is not code, it’s trust. Scammers exploit the spirit and curiosity of their community to exploit goodwill.”
He said attackers embed themselves in the community, learned about the culture, imitated trustworthy friends, then went on strike.
Gabi Urrutia, chief information security officer at cybersecurity firm Halborn, told Cointelegraph that the scam combines social engineering with malware, and although not “very refined,” it is a conspiracy due to “abuse of trust among community members.”
“While it’s not as important as the traditional phishing of volumes, it’s more and more frequent in Web3 and the gaming community, and there’s a mix between pair-to-pair trust and high-value assets,” he said.
“The key here is psychological manipulation. Attackers begin to become part of the community, learn slang and introduce them as friends.”
Scammer tactics move past the code
In February, a user under the handle posted to the malware beat forum that someone who thought a friend had sent the link had fallen prey to a “notorious scam.” The Reddit Forum, which began in July, also warned of scams targeting gamers.
Percoco told Cointelegraph that the crypto industry tends to see these scams first, but tactics will spread across the sector.
He said the best way to avoid being trapped is to have “healthy skepticism,” check your identity through another channel, avoid running unknown software, and remember that “doing nothing is safer than taking a dangerous step.”
“If something feels rushed, generous, or untrue, it’s almost always the case. Don’t trust it, check it out.”
Urrutia said defense against this scam involves very specific habits, such as stopping thinking before signing anything, minimizing privileges and using the same device to manage your gaming and wallet.
“And from the community side, it also limits direct messages from strangers, validates new members, and strengthens the security culture. Ultimately, the major challenges aren’t technical, but not cultural,” he added.
Fake recruiting campaigns are even worse
However, Percoco also said that Crypto’s wider trends now involve fake recruiters while discordant scams are on the rise.
Related: North Korean hackers target crypto developers with fake recruitment tests
In a recent June case, North Korea-aligned threat actors targeted job seekers in the crypto industry using malware designed to steal passwords for crypto wallets and password managers.
“While discordant spoofing is rising rapidly, the most widespread trend we track today is fake recruitment campaigns where victims are seduced by job offers and fooled into clicking on phishing links,” Percoco says.
Meanwhile, Ultia said the maximum volume of fraud involving Halborn blind signatures, approval phishing and more is all “an evolution of the same idea.”
“A recent highly publicized case was a bibit attack that utilized blind signatures and blind permission management to discharge funds.”
magazine: XRP ‘Cycle Target’ $20, Strategic Bitcoin Lawsuit Dismissed: Hodler’s Digest, August 24-30